Ranger Authorization
Apache Ranger is a security framework used for monitoring, enabling services, and comprehensive data security access management on the Hadoop platform. After using Ranger, permissions configured on the Ranger side replace the execution of Grant statements in Doris for authorization. For Ranger installation and configuration, see below: Installing and Configuring Doris Ranger Plugin.
Ranger Example
Change Doris Configuration
- In the
fe/conf/fe.conffile, configure the authorization method asranger access_controller_type=ranger-doris. - In the
fe/conf/ranger-doris-security.xmlfile, configure the basic information of Ranger. - Start the cluster.
Permission Example
- Create
user1in Doris. - In Doris, first use the
adminuser to create a Catalog:hive. - Create
user1in Ranger.
Global Permissions
Equivalent to the internal Doris authorization statement grant select_priv on *.*.* to user1;
-
The global option can be found in the dropdown box at the same level as the catalog.
-
Only
*can be entered in the input box.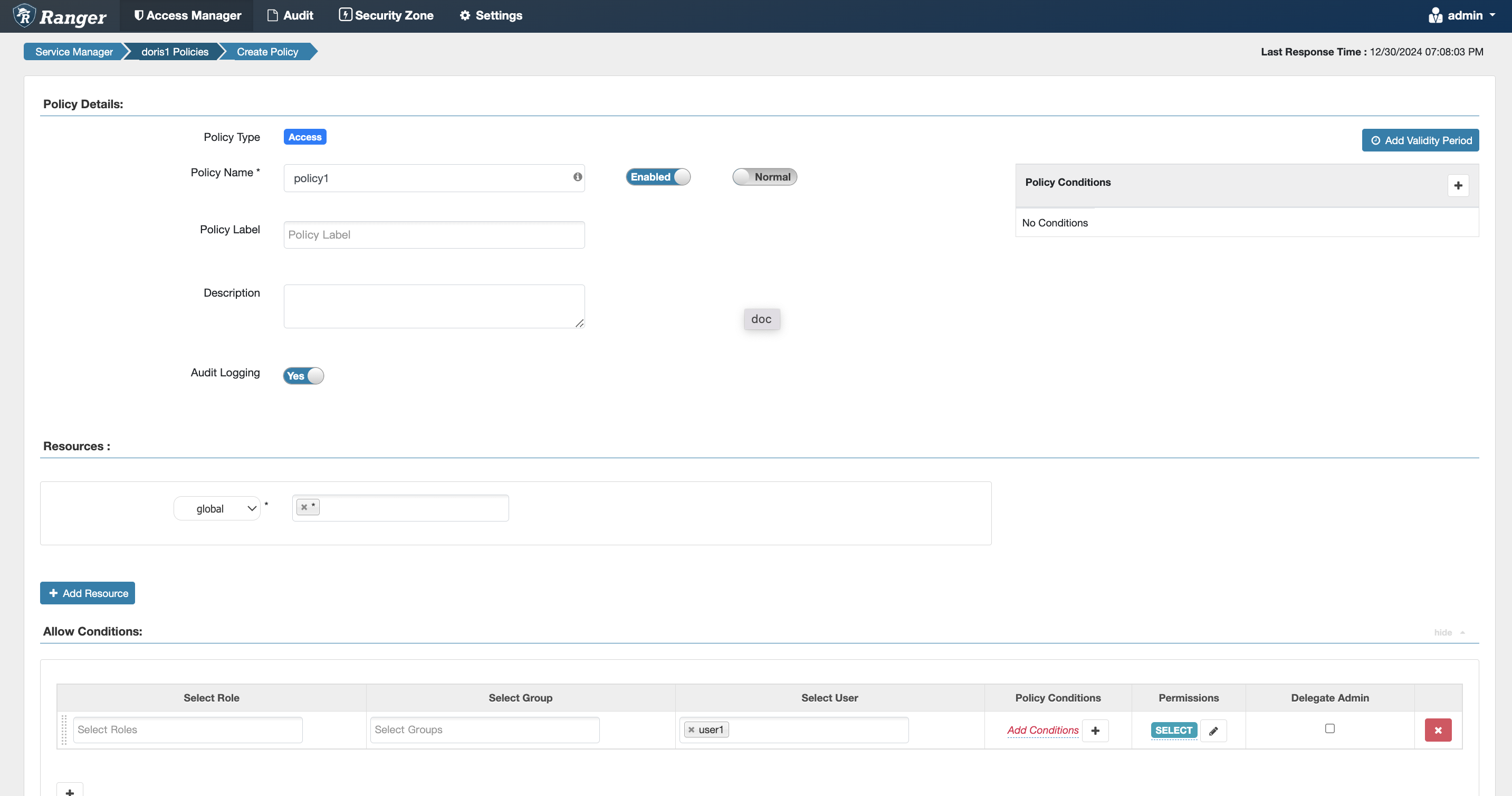
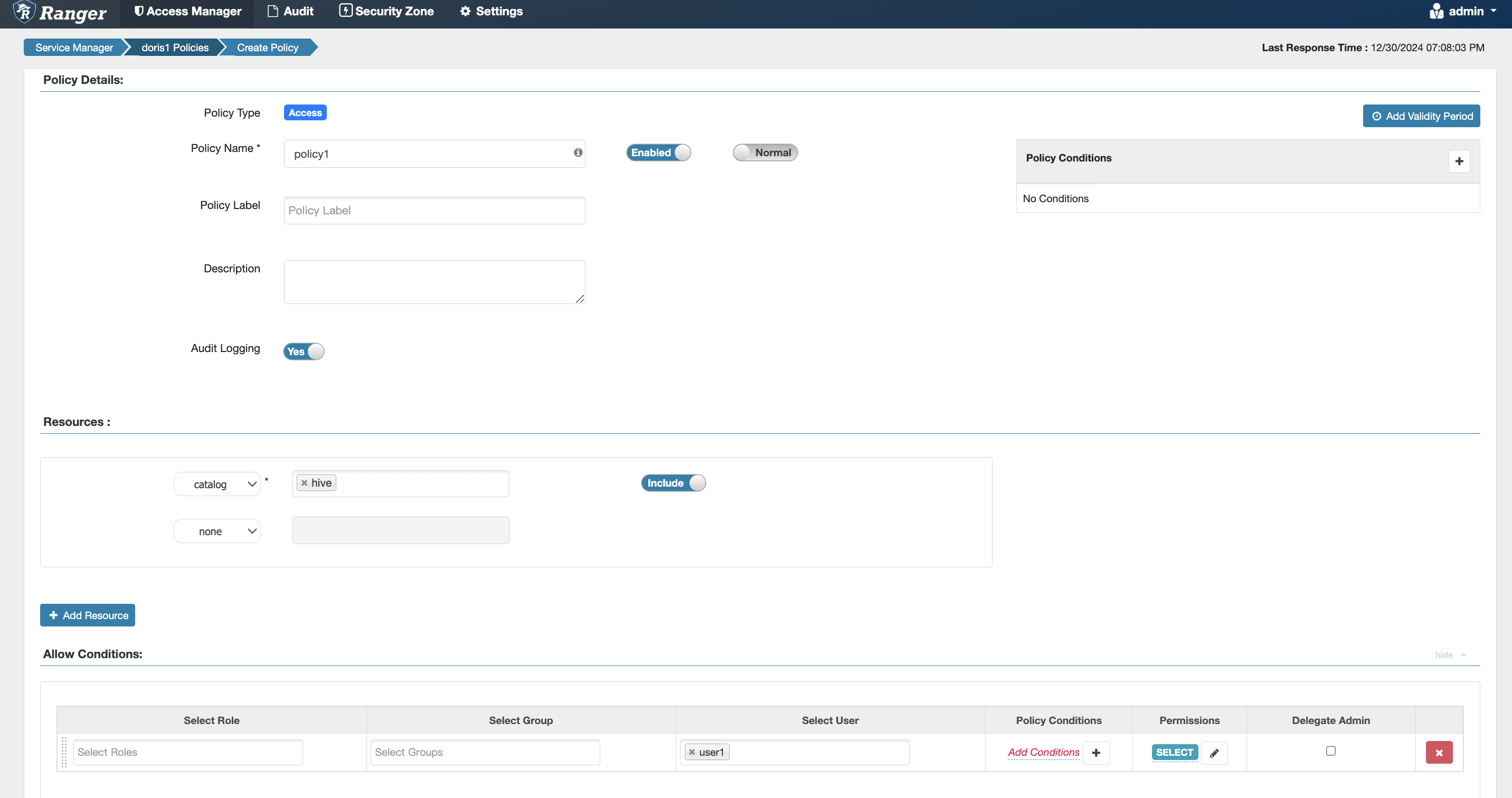
Catalog Permissions
Equivalent to the internal Doris authorization statement grant select_priv on hive.*.* to user1;
Database Permissions
Equivalent to the internal Doris authorization statement grant select_priv on hive.db1.* to user1;
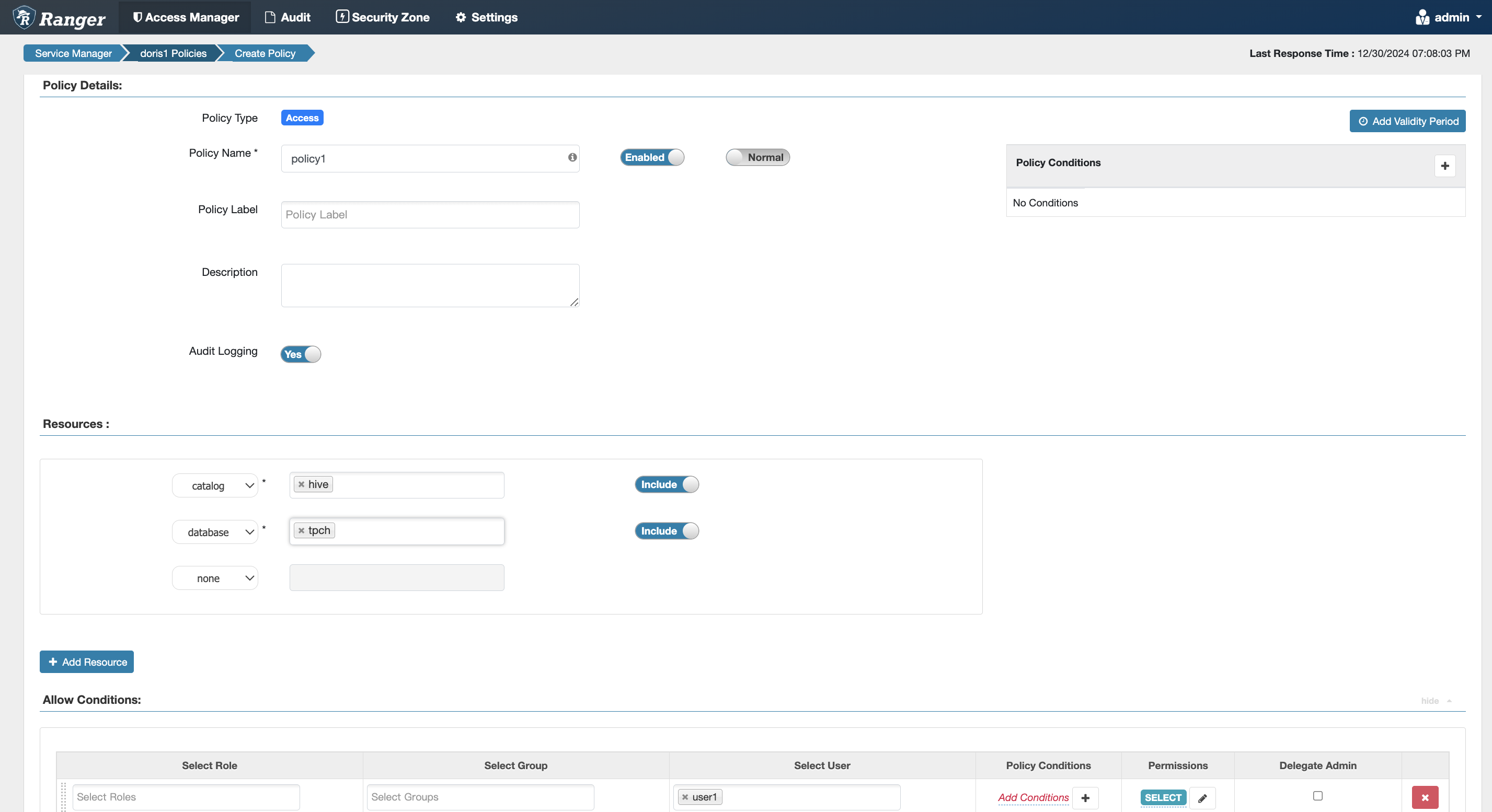
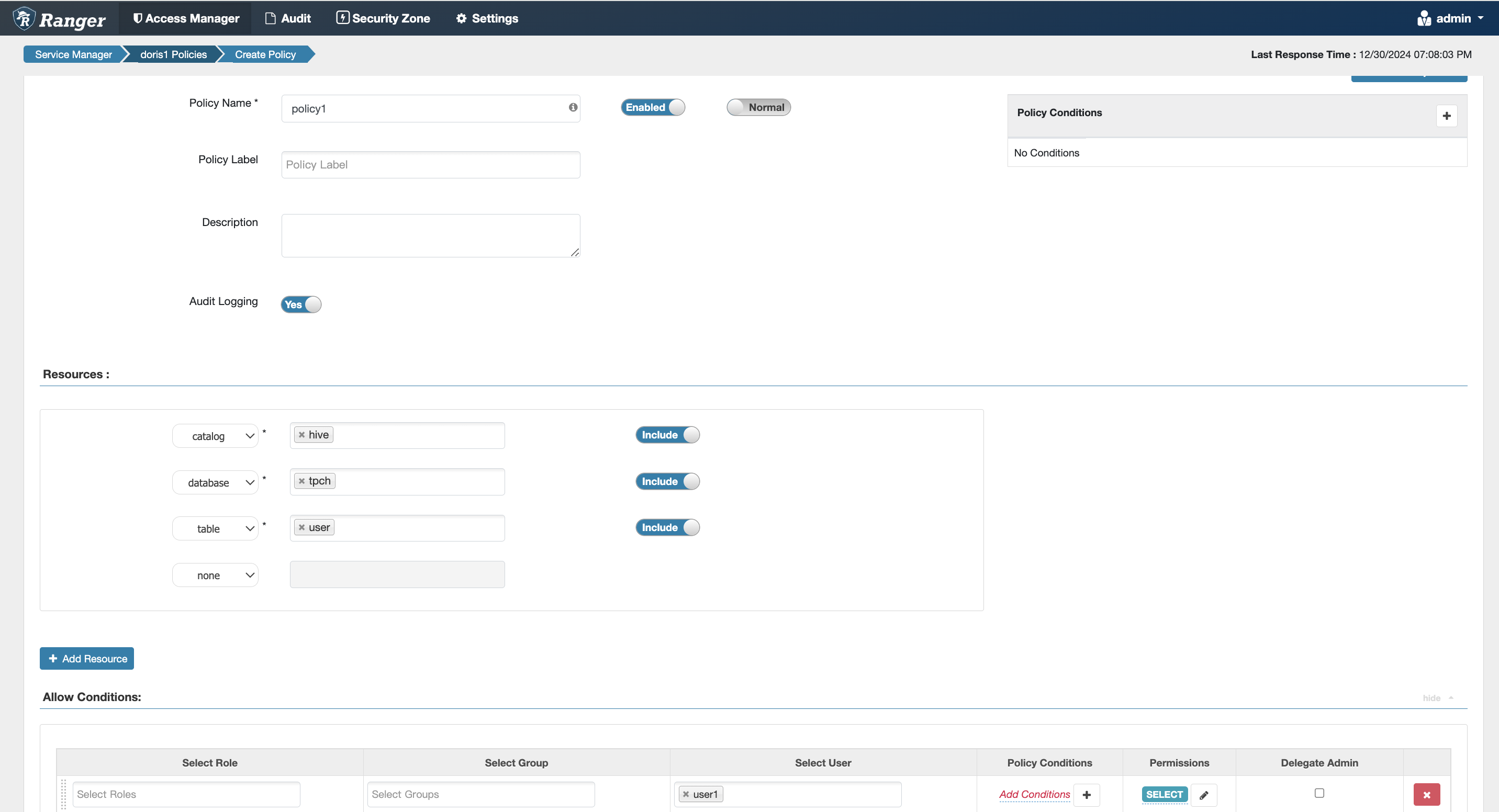
Table Permissions
Equivalent to the internal Doris authorization statement grant select_priv on hive.db1.tbl1 to user1;
Column Permissions
Equivalent to the internal Doris authorization statement grant select_priv(col1,col2) on hive.db1.tbl1 to user1;
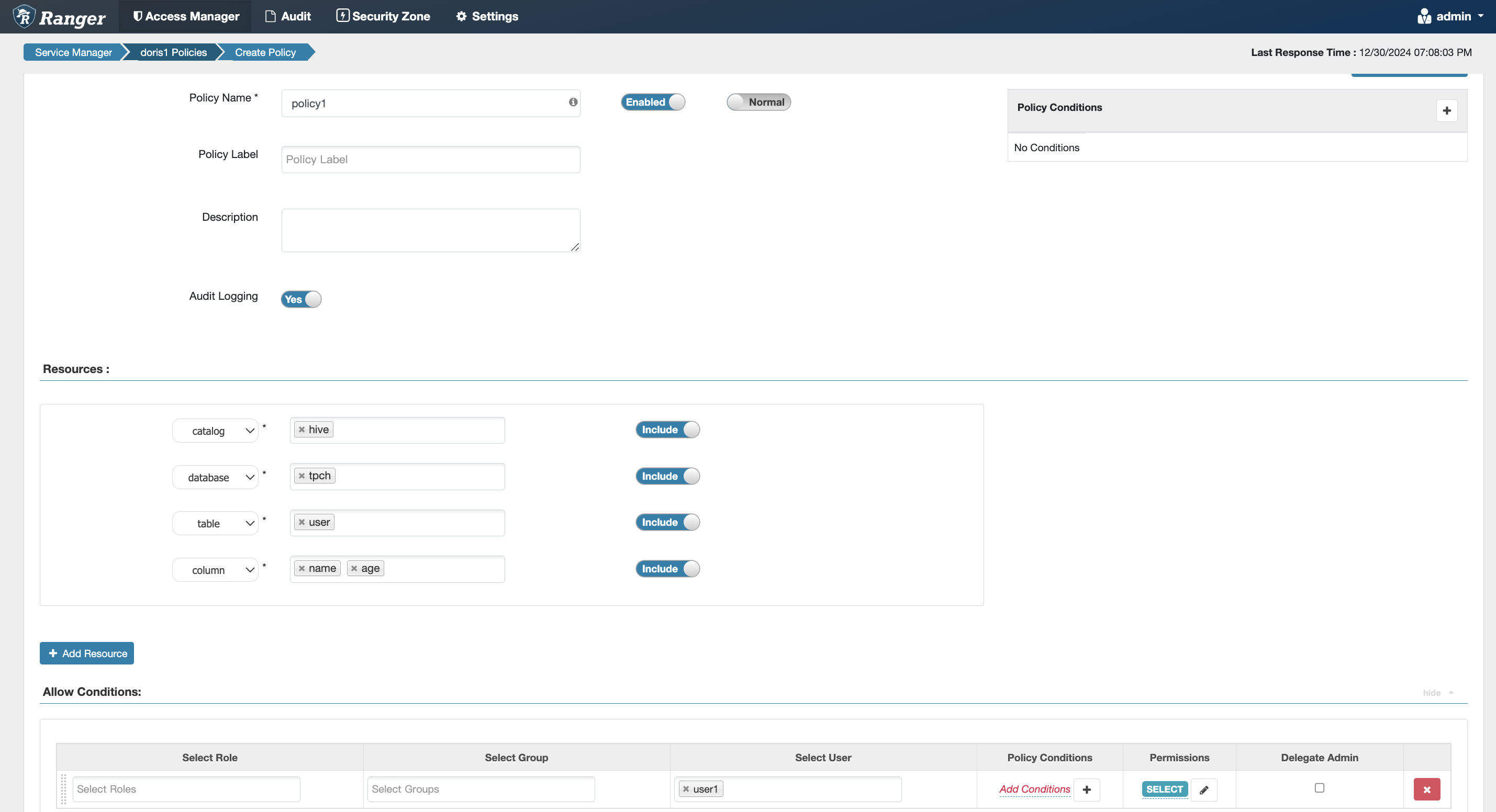
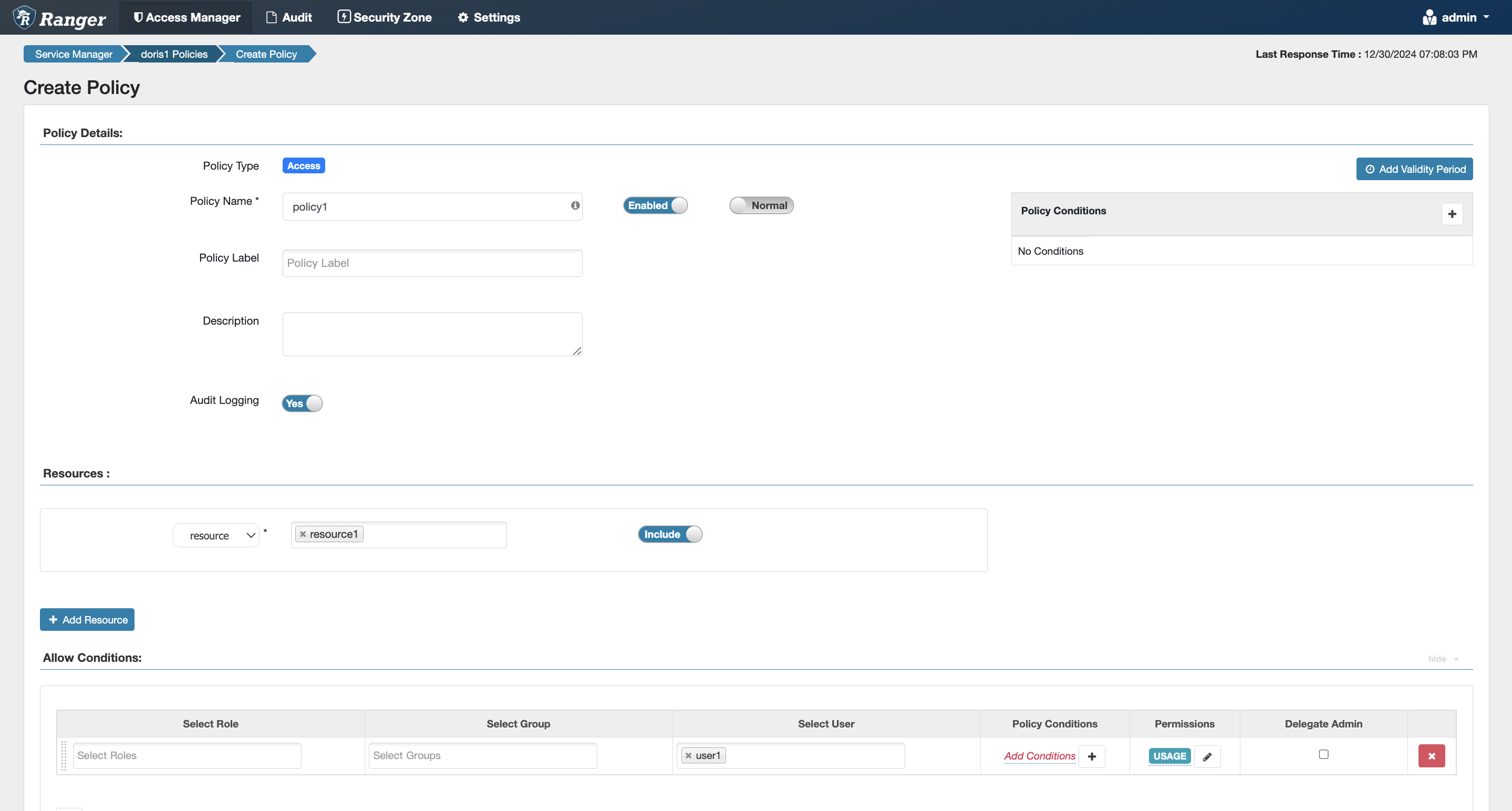
Resource Permissions
Equivalent to the internal Doris authorization statement grant usage_priv on resource 'resource1' to user1;
- The resource option can be found in the dropdown box at the same level as the catalog.
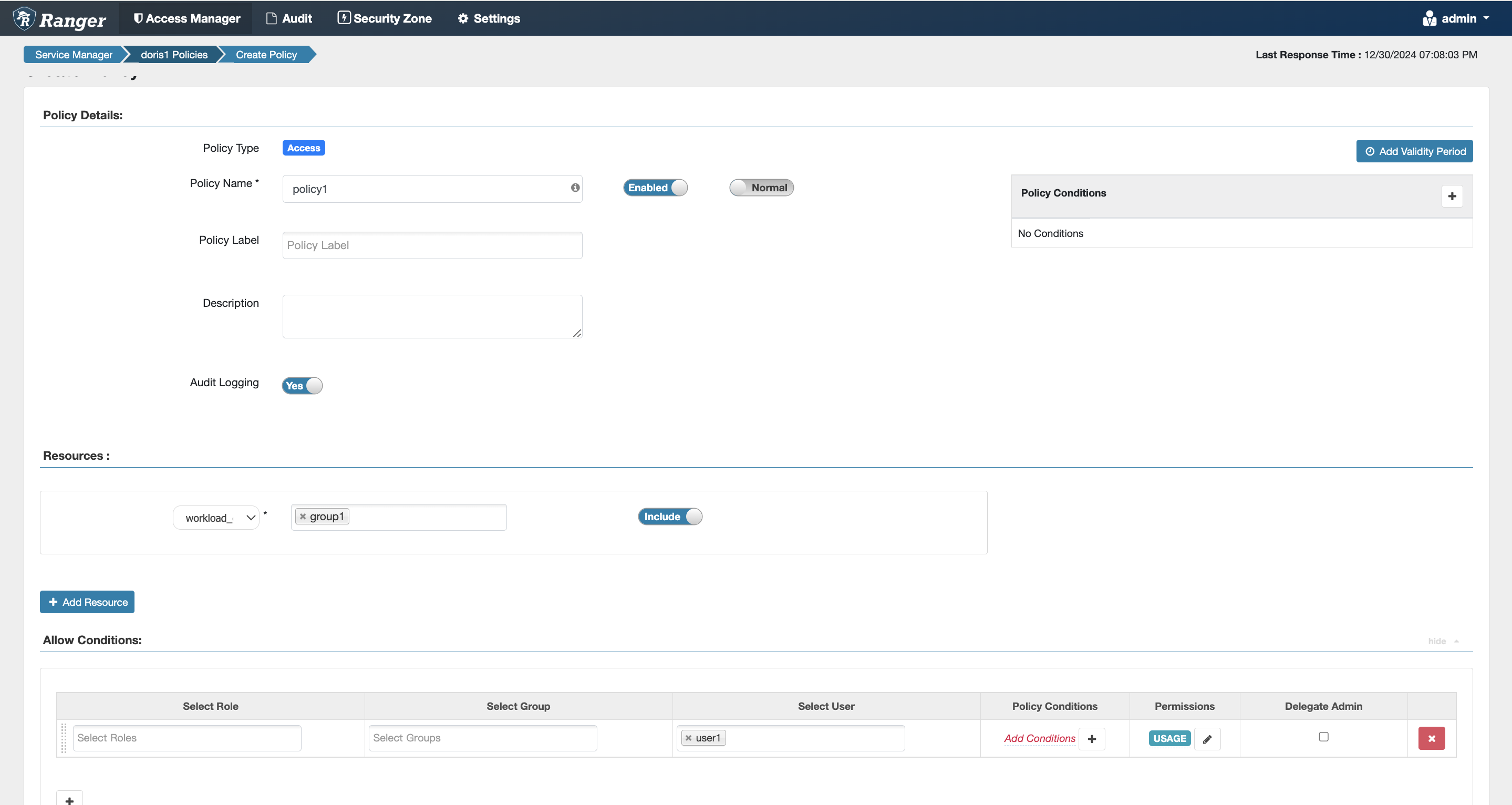
Workload Group Permissions
Equivalent to the internal Doris authorization statement grant usage_priv on workload group 'group1' to user1;
- The workload group option can be found in the dropdown box at the same level as the catalog.
Row-Level Permissions Example
Supported in version 2.1.3
-
Refer to the permission example to grant
user1the select permission on theinternal.db1.usertable. -
In Ranger, add a Row Level Filter policy
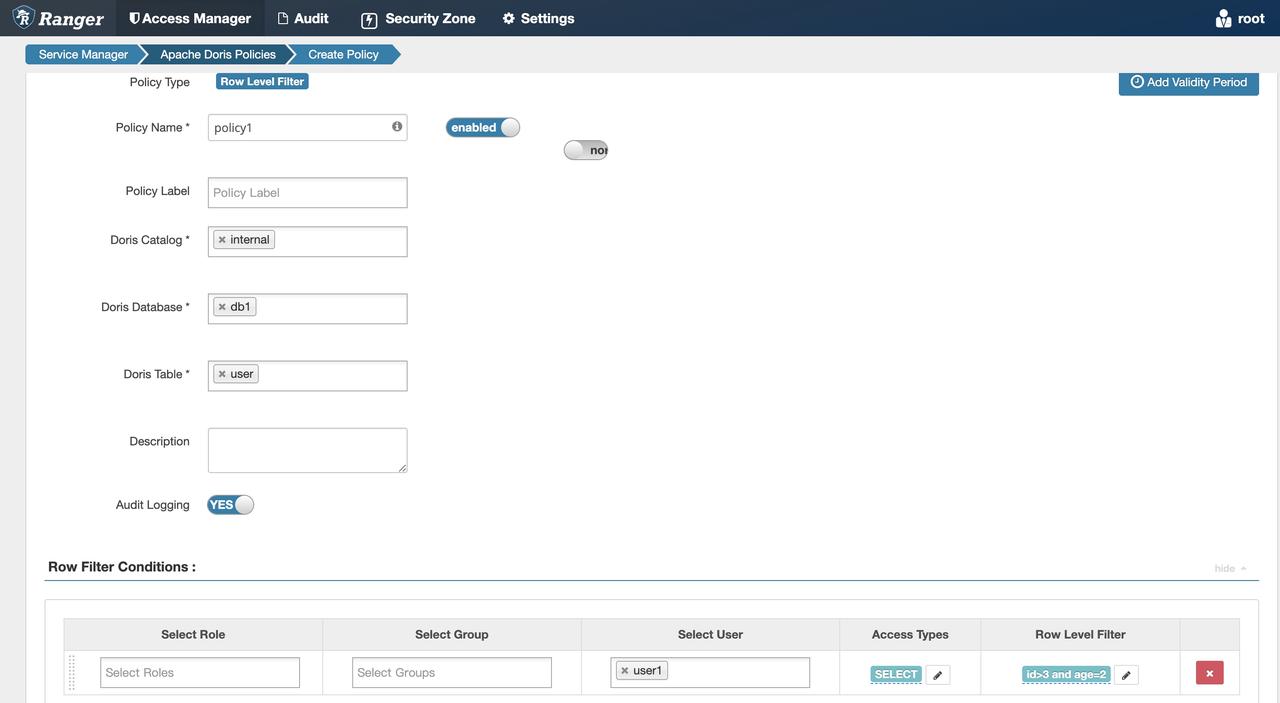
-
Log in to Doris with
user1. Executeselect * from internal.db1.user, and only see the data that meets the conditionid > 3andage = 2.
Data Masking Example
Supported in version 2.1.3
-
Refer to the permission example to grant
user1the select permission on theinternal.db1.usertable. -
In Ranger, add a Masking policy
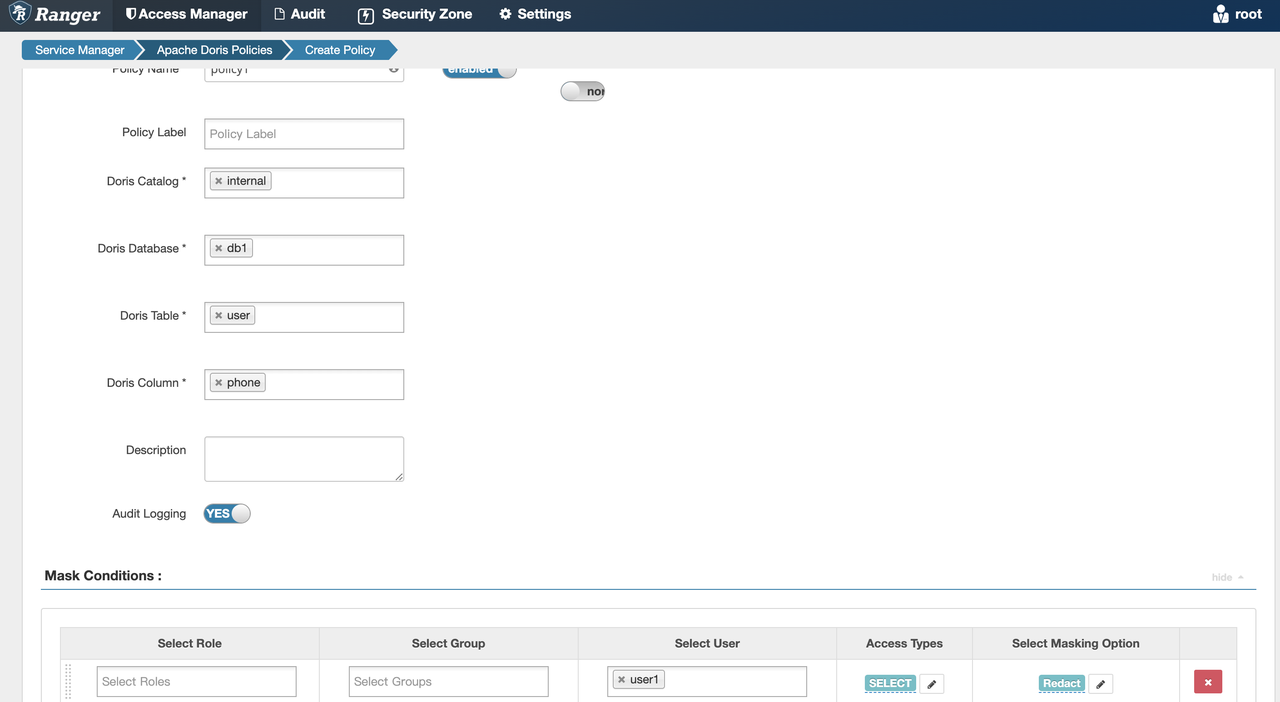
-
Log in to Doris with
user1. Executeselect * from internal.db1.user, and see the phone number is masked according to the specified rule.
Frequently Asked Questions
-
How to view the log when Ranger access fails? Create a
log4j.propertiesfile in theconfdirectory of all FEs, with the following content:log4j.rootLogger = warn,stdout,D
log4j.appender.stdout = org.apache.log4j.ConsoleAppender
log4j.appender.stdout.Target = System.out
log4j.appender.stdout.layout = org.apache.log4j.PatternLayout
log4j.appender.stdout.layout.ConversionPattern = [%-5p] %d{yyyy-MM-dd HH:mm:ss,SSS} method:%l%n%m%n
log4j.appender.D = org.apache.log4j.DailyRollingFileAppender
log4j.appender.D.File = /path/to/fe/log/ranger.log
log4j.appender.D.Append = true
log4j.appender.D.Threshold = INFO
log4j.appender.D.layout = org.apache.log4j.PatternLayout
log4j.appender.D.layout.ConversionPattern = %-d{yyyy-MM-dd HH:mm:ss} [ %t:%r ] - [ %p ] %m%nChange
log4j.appender.D.Fileto the actual path, which is used to store the Ranger plugin log.
Install and Configure Doris Ranger Plugin
Install Plugin
-
Download the following files
-
Place the downloaded files in the
ranger-plugins/dorisdirectory of the Ranger service, such as:/usr/local/service/ranger/ews/webapp/WEB-INF/classes/ranger-plugins/doris/ranger-doris-plugin-3.0.0-SNAPSHOT.jar
/usr/local/service/ranger/ews/webapp/WEB-INF/classes/ranger-plugins/doris/mysql-connector-java-8.0.25.jar -
Restart the Ranger service.
-
Download ranger-servicedef-doris.json
-
Execute the following command to upload the definition file to the Ranger service:
curl -u user:password -X POST \
-H "Accept: application/json" \
-H "Content-Type: application/json" \
http://172.21.0.32:6080/service/plugins/definitions \
-d@ranger-servicedef-doris.jsonReplace the username and password with the actual login credentials for the Ranger WebUI.
The service address and port can be found in the
ranger-admin-site.xmlconfiguration file, in theranger.service.http.portconfiguration item.If the execution is successful, a JSON-formatted service definition will be returned, such as:
{
"id": 207,
"guid": "d3ff9e41-f9dd-4217-bb5f-3fa9996454b6",
"isEnabled": true,
"createdBy": "Admin",
"updatedBy": "Admin",
"createTime": 1705817398112,
"updateTime": 1705817398112,
"version": 1,
"name": "doris",
"displayName": "Apache Doris",
"implClass": "org.apache.ranger.services.doris.RangerServiceDoris",
"label": "Doris",
"description": "Apache Doris",
"options": {
"enableDenyAndExceptionsInPolicies": "true"
},
...
}If you want to recreate the service definition, you can use the following command to delete the service definition and then re-upload it:
curl -v -u user:password -X DELETE \
http://172.21.0.32:6080/service/plugins/definitions/207Replace
207with the actual ID returned when creating the service definition.Before deleting, you need to delete the Doris service created in the Ranger WebUI.
You can also use the following command to list the current service definitions and get the ID:
curl -v -u user:password -X GET \
http://172.21.0.32:6080/service/plugins/definitions/
Configure Plugin
After installation, open the Ranger WebUI, and you can see the Apache Doris plugin in the Service Manager interface:
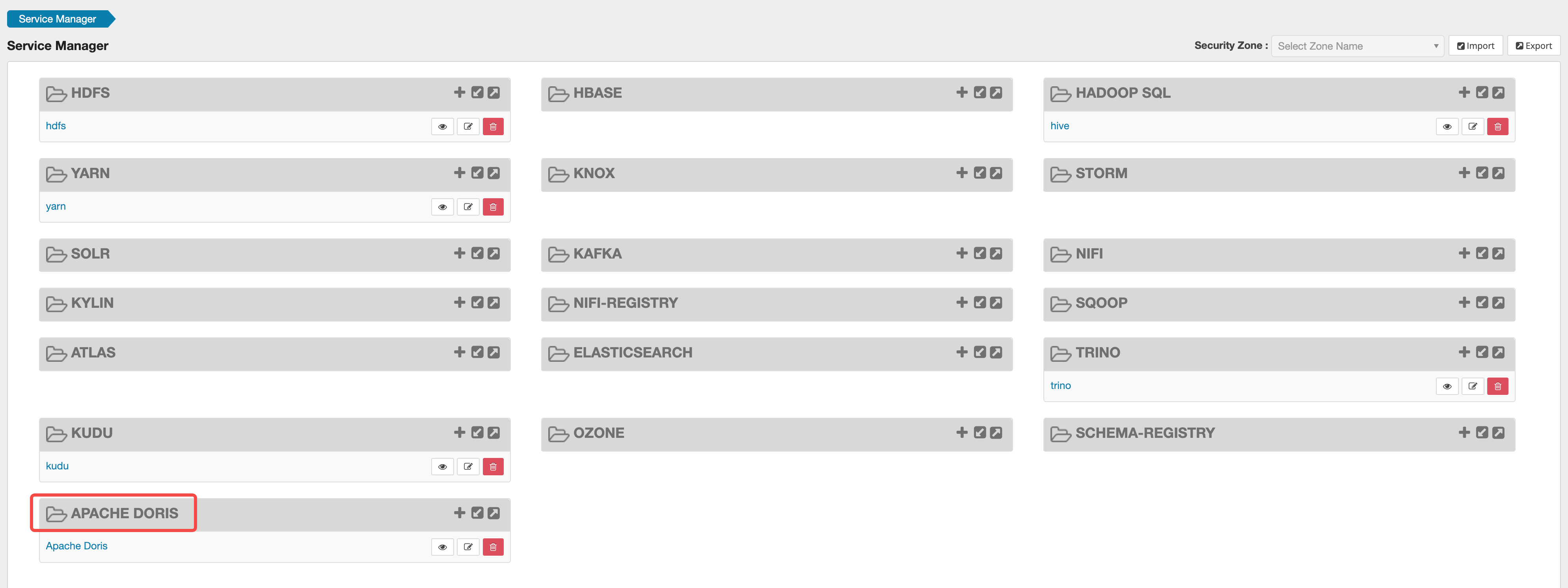
Click the + button next to the plugin to add a Doris service:
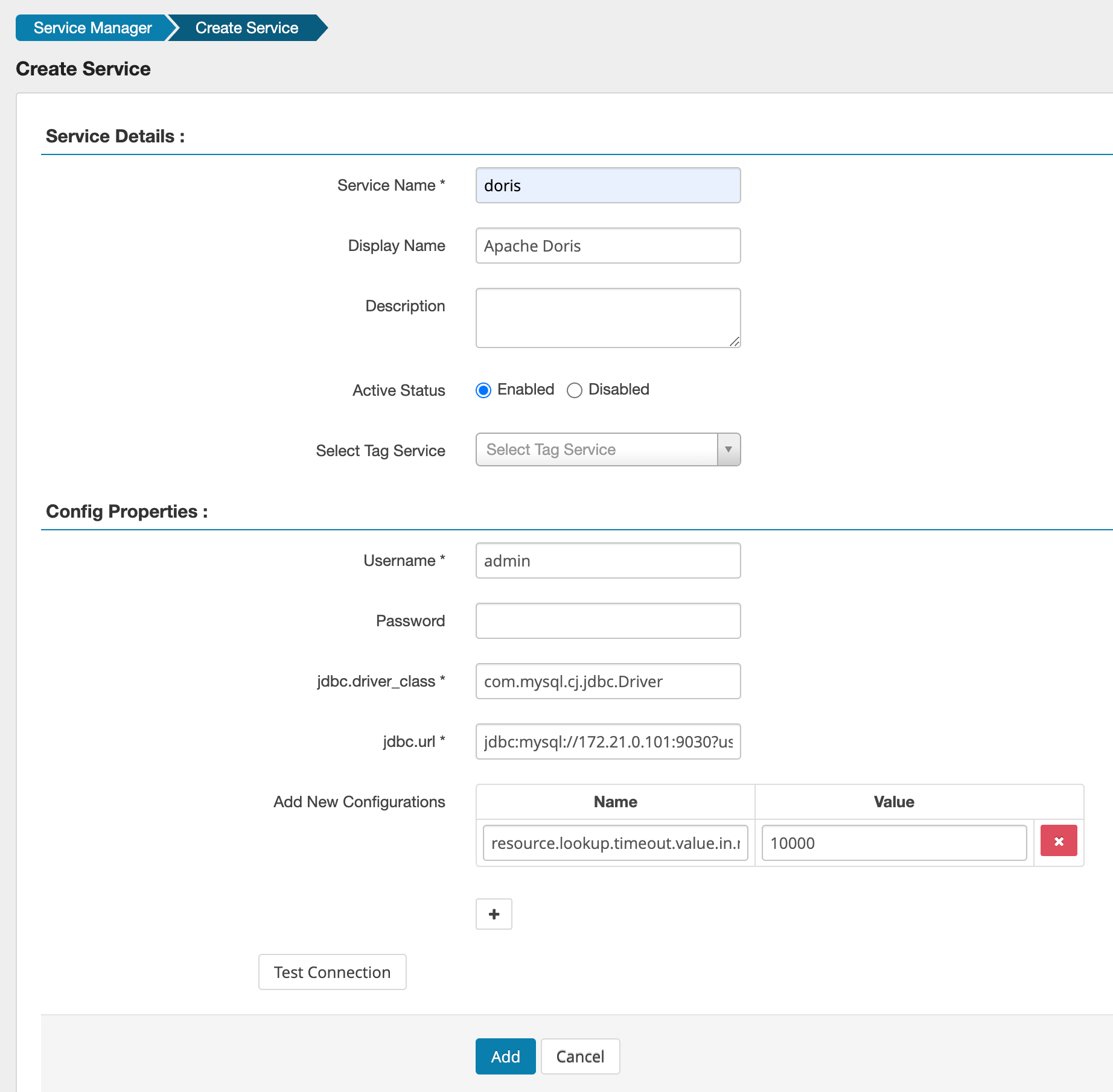
The Config Properties section has the following parameters:
Username/Password: The username and password of the Doris cluster. It is recommended to use the Admin user.jdbc.driver_class: The JDBC driver used to connect to Doris.com.mysql.cj.jdbc.Driverjdbc.url: The JDBC URL connection string of the Doris cluster.jdbc:mysql://172.21.0.101:9030?useSSL=false- Additional parameters:
resource.lookup.timeout.value.in.ms: The timeout for getting metadata, recommended to set to10000, which is 10 seconds.
You can click Test Connection to check if the connection is successful.
After clicking Add, you can see the created service in the Service Manager interface of the Apache Doris plugin. Click the service to start configuring Ranger.

